
Aftershave, Perfume and Baked Beans. Commuting routes and Jobs. Brexit.
People dread change in their day to day lives.
Windows XP – no one wanted to give that up, and now we are seeing the same reluctance with Windows 7 – Just shows how right Microsoft can get it sometimes.
Passwords are difficult to give up as well. The tolling bell of daily notifications in the bottom right of the screen telling them that it is expiring imminently. They dismiss this until the morning that they cannot put it off any longer and then choose a well-used one from another account that they have used before.
While this may give them some sense of continuity, and ease the turmoil every 90 days or so, it can also become a predictable dance that a person could allow themselves to fall into. Clients bemoan the need to choose new passwords when we reset them when a forgotten password denies them access to their systems. All they want to do is to open their PC and put in their day’s work and shut it down at the end of the day. Surely their little bit of what they access can’t be of interest to anyone else?
As we know, and as I patiently explain to every user that I have this conversation with, a chink in an organisation’s security can, and will, be sought out and exploited by those wishing to do mischief or harm.
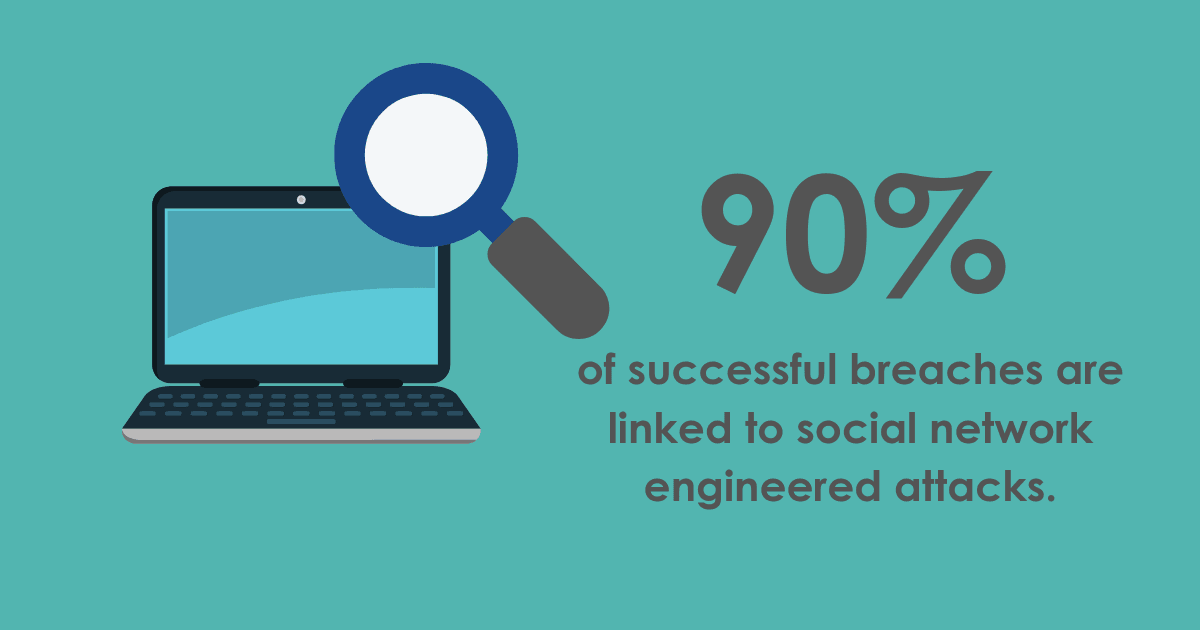
The figures for social network engineered attacks on organisations accounted for over 90% of all successful breaches. Over 30% of UK businesses have reported an attack in the last 12 months.
So, reusing a password from an online gaming account for your work email may seem a reasonable idea, but with social engineering and building of online profiles it puts these 2 accounts in proximity and your level 99 Rogue becomes the key to your organisation’s servers.
While this situation is avoidable, people still do exactly the above as the resistance to change is greater than the perceived need to secure their accounts well.
The helpdesk imperative is to tip the scales of this resistance and help staff to appreciate that all their accounts matter. Helping them understand this is a major boost to any organisation’s cyber security. So, while the company firewall may be impenetrable, if the helpdesk is speaking to staff that aren’t aware of the security risk that all user accounts pose, then those staff are an opportunity for attackers to manipulate and convince to handing over their security credentials. Are your staff the hard, outer shell protecting you or the soft underbelly unprepared for attack?
But staff cannot be expected to know what is safe or not. Email do not come colour coded with big yellow and black stripes warning them that this is not safe to open. They come promising cash rewards from far off lands, or warnings of accounts that have been compromised and, helpfully, offering a link to repair these accounts. Victims of deceit are seldom complicit. These types of emails may be clumsy and obvious to some, but to others who may not have come across them before, may just be curious enough to click the link.
Security awareness training can help with identifying those staff that need assistance and can help an organisation identify where defences, if tested, are likely to leak. Investing in staff training and giving them the tools to make them aware of their role in the defence of the organisation engages people and makes them feel valued. Staff who feel valued and invested in by their organisation go further to protect it.
While the helpdesk can promote password hygiene and good password practices to staff who call, they cannot give the depth of training needed to every user that would be required to provide an organisation with the robust first line of defence.
A well informed and trusted roster of employees is as necessary to an organisation’s defence as a firewall and should be treated with the same level of ongoing support. Where a firewall will have rules of what is allowed in and out and is updated on a regular basis of sites and domains that are malicious in their intent, staff will need continuing support as new, more convincing attacks are presented to them.
Whether a long lost relative is asking for assistance moving large amounts of cash or Apple is advising them that their iTunes account has expired, and they should click on the link provided to reset their account, they will have the knowledge of how these types of invitations should be treated. And, when their password next comes up for renewal, they would be confident to select a new password, based on their knowledge of the security implications of that choice, and not dread it.
We always recommend a multi-layered approach to cyber security, find out about our cyber security solution here!
Visit our free cyber security resources pages to educate your teams and protect your education.
or alternatively contact us today to discuss all things cyber security.
This blog was written by Adrian, a member of the helpdesk team.



