Though the infection phase is slightly different for each ransomware version, the key stages are the following:
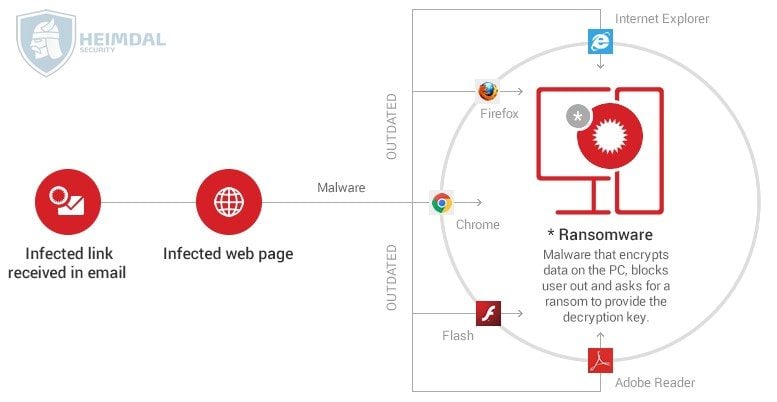
Initially, the victim receives an email which includes a malicious link or a malware-laden attachment. Alternatively, the infection can originate from a malicious website that delivers a security exploit to create a backdoor on the victim’s PC by using a vulnerable software from the system.
If the victim clicks on the link or downloads and opens the attachment, a downloader (payload) will be placed on the affected PC.
The downloader uses a list of domains or C&C servers controlled by cyber criminals to download the ransomware program on the system.
The contacted C&C server responds by sending back the requested data, in our case, the ransomware.
The ransomware starts to encrypt the entire hard disk content, personal files and sensitive information. Everything, including data stored in cloud accounts (Google Drive, Dropbox) synced on the PC. It can also encrypt data on other computers connected in the local network.
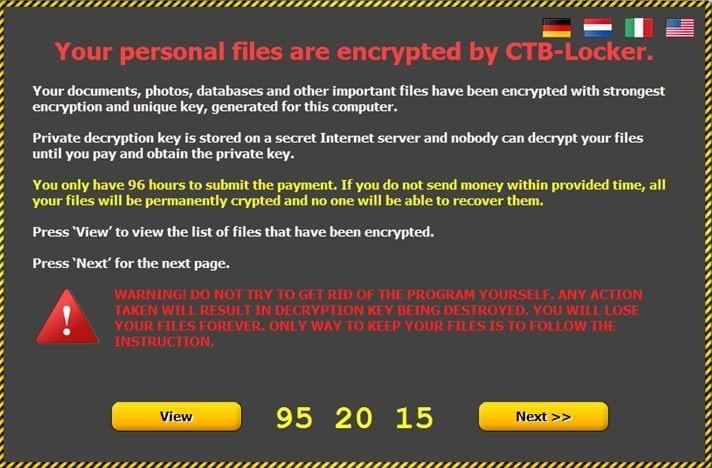
A warning pops up on the screen with instructions on how to pay for the decryption key.
To ensure your business is as safe as possible from ransomware attacks, take a look at this blog on How to Protect your Business from a Ransomware Attack
Call us on 01628 552 860 or email enquiries@complete-it.co.uk to book a meeting.



