
Missed our live webinar on how to spot a phishing email? No worries, you can catch up on the highlights of the webinar or follow the link to the webinar below.
What was covered?…
WHAT IS PHISHING?
Phishing has evolved overtime, it started from the obvious fake emails from your long lost auntie in Texas (that you know doesn’t exist) asking for some money to the sophisticated hackers of today who impersonate people and brands we know so well that sometimes it feels impossible to distinguish, real from fake.
SETTING THE TRAP
The discussion then moves onto how hackers craft their emails and some examples are given. One example being that a hacker could pretend to send an email from your HR department stating you have been awarded a £25 Amazon voucher for meeting your targets this month. This being something that happens each month and isn’t ringing any alarm bells.
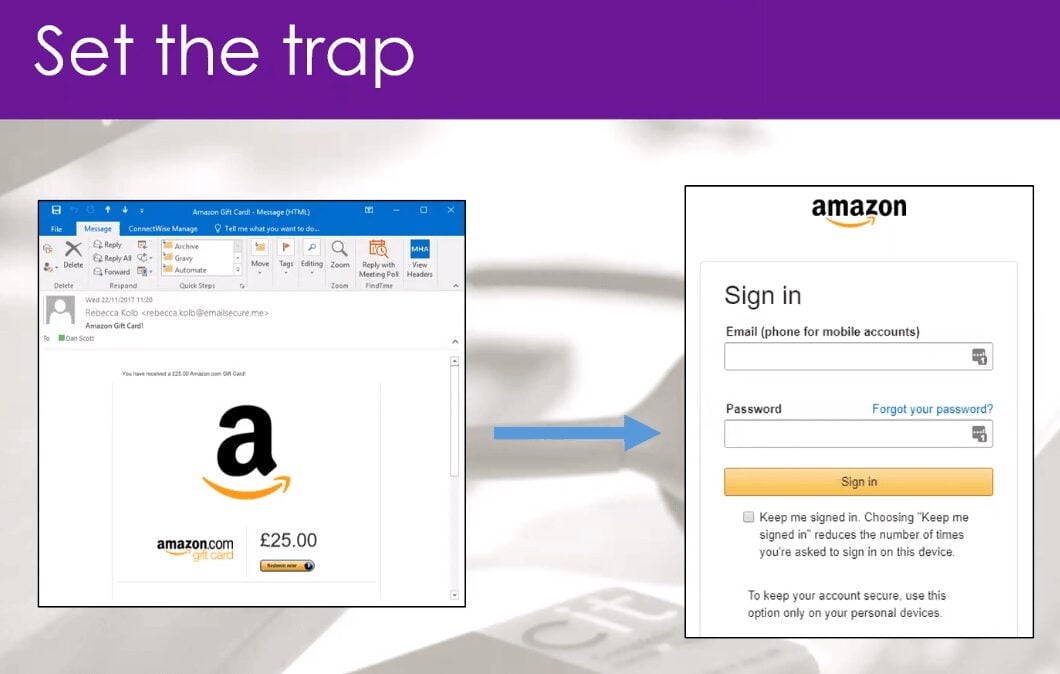
It is explained that when you have lots to, the email appears to be legit or you may be stressed and just want to get through your inbox, it is easy to make mistakes and not realise you are responding to a phishing email. It is important to always be alert as upon closer inspection you can see that the above email address is not correct (not from @complete-it.co.uk) and amazon.com instead of amazon.co.uk has been used, small errors that often can be easily overlooked.
Tactics that hackers use when they are creating an email are discussed and include the below.
- Fear and scare tactics – Hackers create a sense of urgency which can make you click on links or attachments as you are sent into panic.
- Imitating a known brand – Hackers have become so sophisticated that they can sometimes imitate a well-known brand pretty much perfectly, which is why it’s important to look out for spelling and grammar mistakes as well as checking the send from email and website addresses as usually these are big give aways.
TRAINING YOUR TEAMS
Lastly the combination of creating a process to educate your teams and installing software is the key. Giving your teams training on how they can spot a phishing email, inform them of the importance of password protection and two-factor authentication and just overall making them aware of what hackers are capable of and the implications to your business are all great steps to protecting your business.



