Complete I.T. Blog

The CIT Newsletter: Microsoft Power Apps and Microsoft Power BI
This month we take a closer look at Microsoft Power Apps and Microsoft Power BI and how these business intelligence solutions are helping our clients to connect data sources, automate processes and simplify reporting. The Microsoft Power Platform Make informed...
Legal Compliance and Your Guest Wireless Network
So, you have a guest wireless network, or have you been considering rolling out one out for the first time? You’ve done the research, and you’re confident about your hardware choices, network management strategy and planned security measures. All the boxes are ticked, and you’ve covered all your bases. Or have you?
Q&A – Top five challenges facing MSPs…and how they can overcome them
What are the main challenges faced by MSPs?
Why does ransomware often go undetected by antivirus?
Not get observed by law enforcement agencies and their own malware researchers.
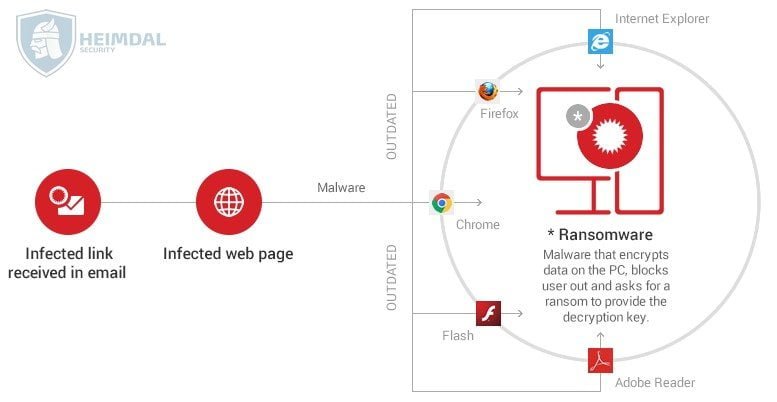
How do ransomware infections happen?
Though the infection phase is slightly different for each ransomware version, the key stages are the following:
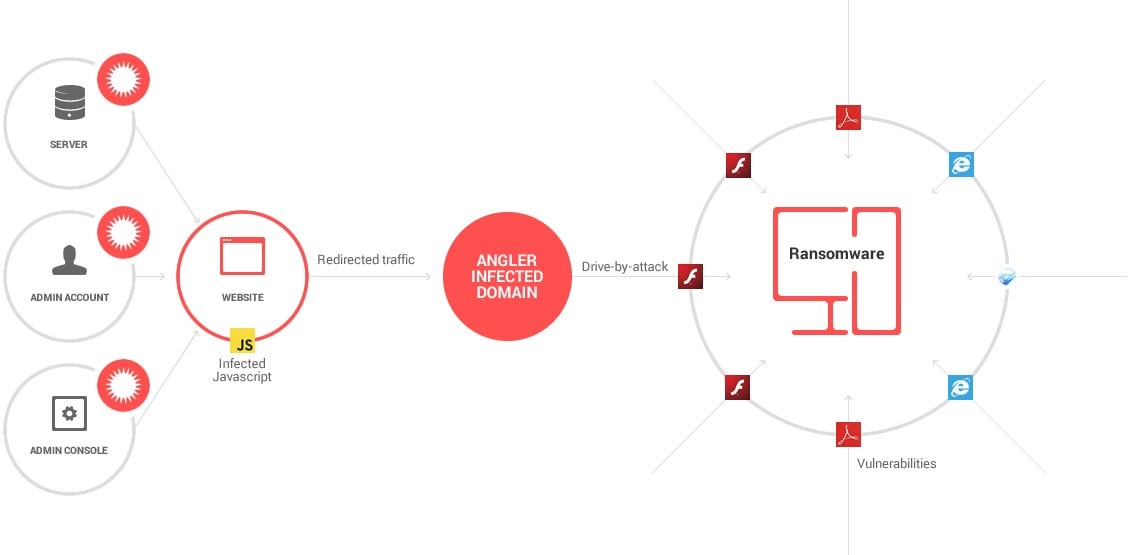
How do ransomware threats spread?
Ransomware and any other advanced piece of financial or data stealing malware spreads by any available means.
Why do ransomware creators and distributors target businesses?
We all know businesses are targeted by Ransomware, but why?
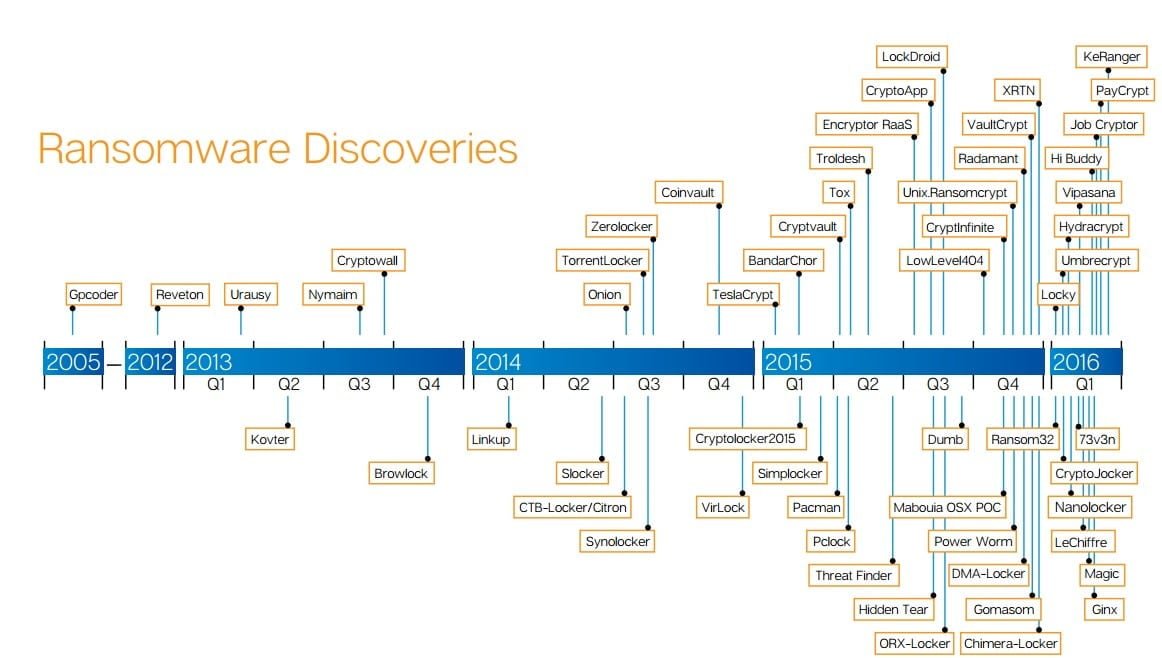
A brief History of Ransomware
It may be difficult to imagine, but the first ransomware in history emerged in 1989 (that’s 27 years ago). It was called the AIDS Trojan, whose modus operandi seems crude nowadays. It spread via floppy disks and involved sending $189 to a post office box in Panama to pay the ransom.
What is Ransomware?
The word Ransomware is everywhere, but what exactly does it mean?
Microsoft are raising their prices, beat the Jan price rise!
Microsoft have announced that starting from the 1st of January 2017, prices are set to increase by as much as 22%, due to the decreasing value of the pound.
An Acquisition for Complete I.T.
We are very excited to announce that as of the 1st October, we have acquired Plus Technologies.